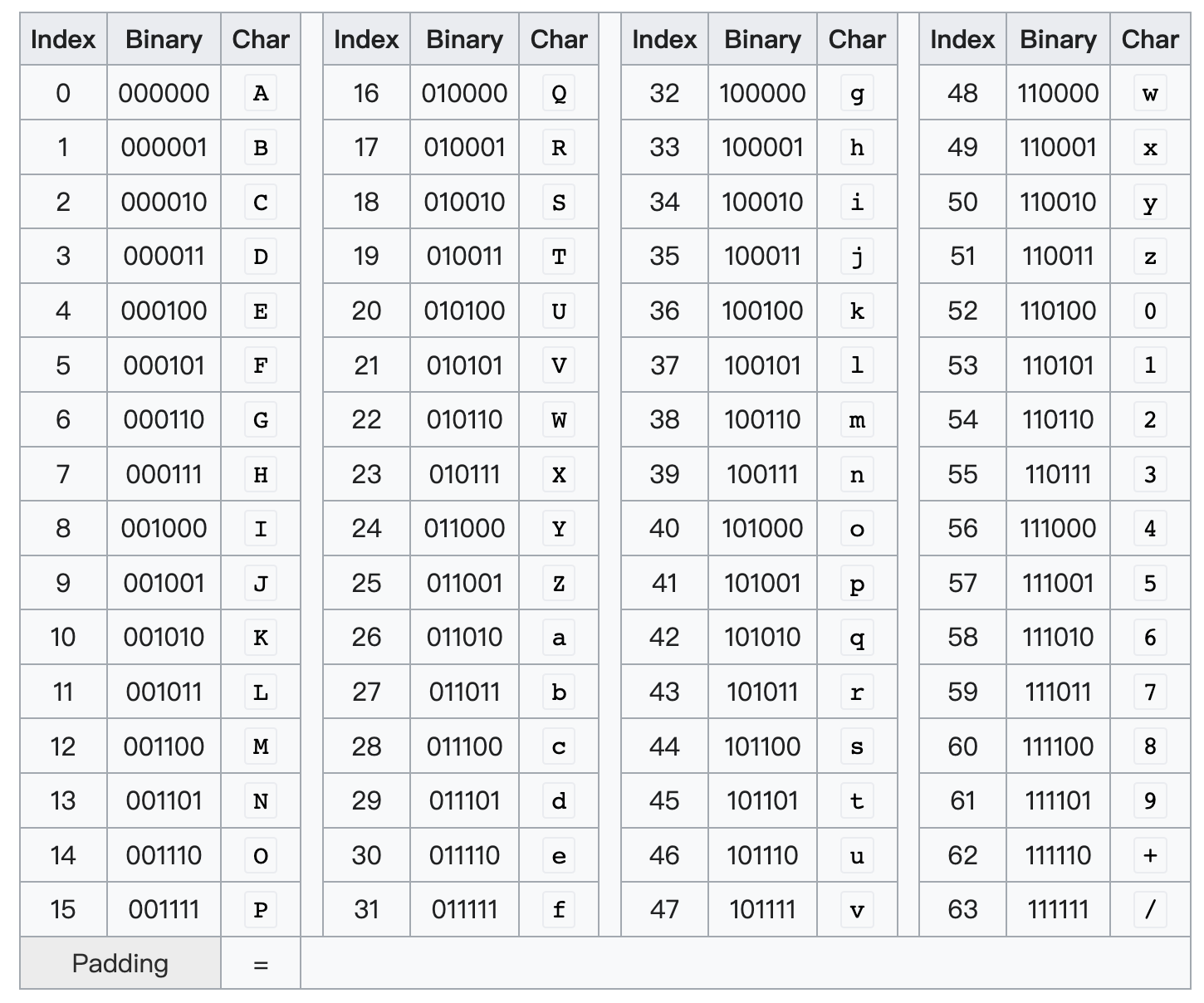
Differences between Encryption, Encoding, and Hashing
March 3, 2023
Encoding
Encoding does not modify data or have any encryption effect; it is simply presented in a different way. The most famous example is Morse code:

The most common encodings used in software development are:
- Base64 encoding
- URL encoding
- ASCII
- Huffman encoding
Below is an example using Base64:
Base64
Base64 encoding is a method of converting binary data to ASCII text, making it easy to transmit over the network or store in a text file. It represents binary data as 64 printable characters, including letters, numbers, and symbols. The encoding process processes three bytes of data at a time and converts them into four printable characters. This makes it a useful encoding scheme for transmitting binary data over a network that only supports text data, such as email. The reverse process of decoding a Base64 string back to its original binary data is also easy.
Encryption
Encryption uses a set of keys to encrypt data. If you need to restore the encrypted data, you also need to use the key to decrypt it. Encryption is divided into symmetric encryption and asymmetric encryption, which are described below.
Symmetric Encryption
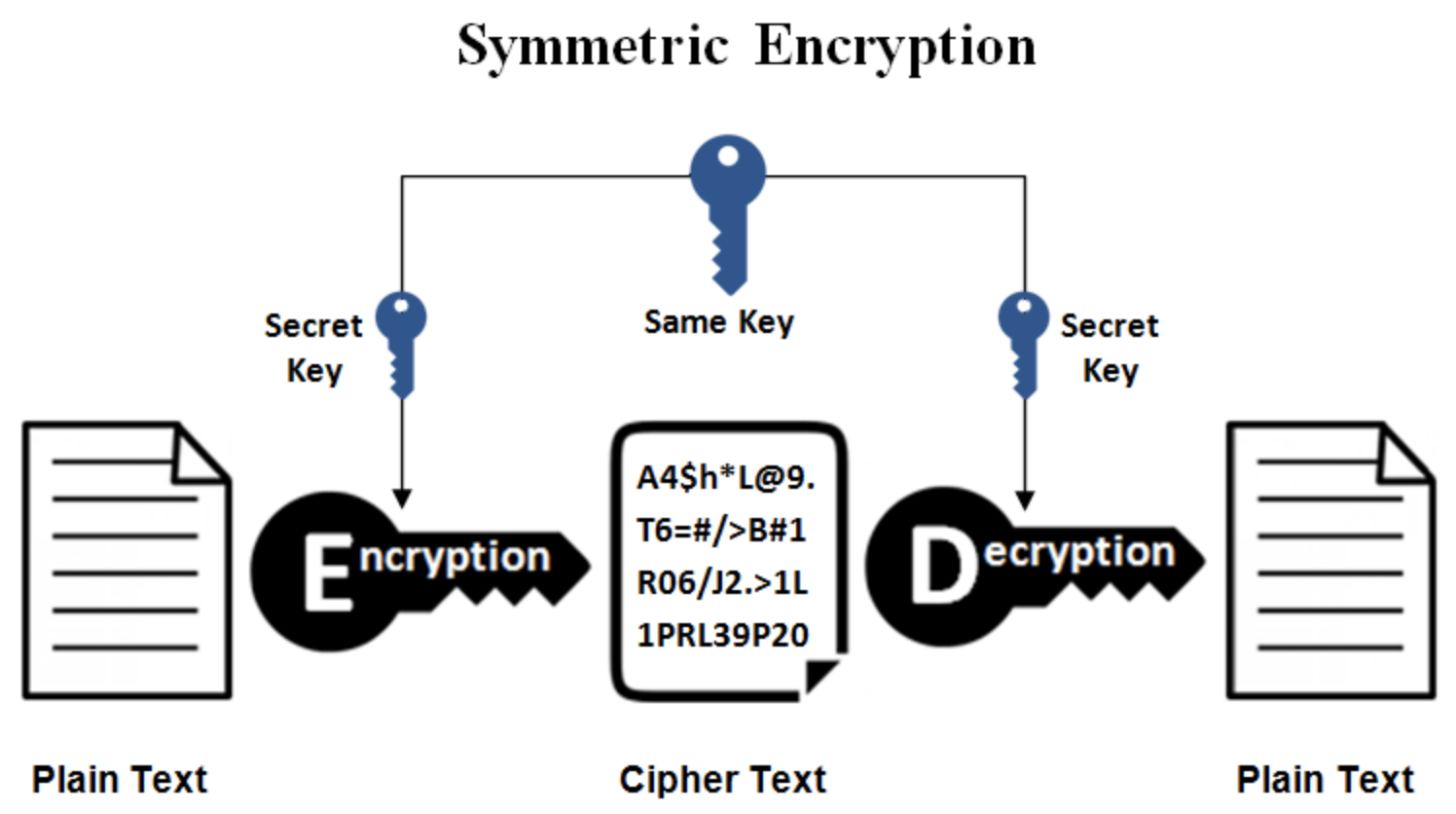
Symmetric encryption uses a single key for encryption and decryption. Therefore, when the message encrypted by symmetric encryption is transmitted, the sender and receiver have the same key. The biggest problem is how to securely transmit the key to the other party and ensure that it will not be intercepted during the process. Common algorithms include AES, DES, and Blowfish.
Asymmetric Encryption
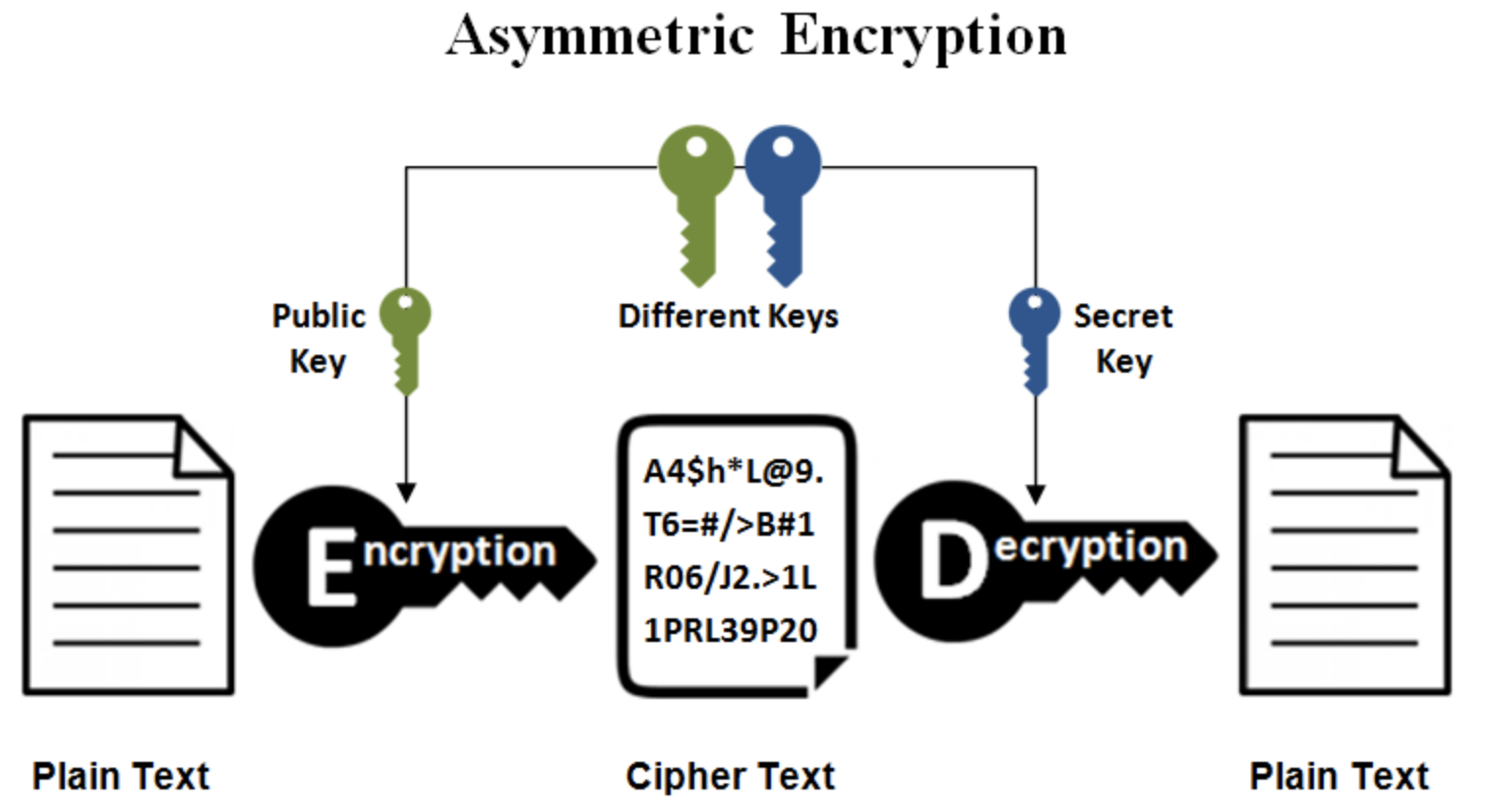
When asymmetric encryption is created, there are two keys: a public key and a private key. The public key is public and can be obtained by anyone, while the private key must be kept secret and can only be used by the owner. The core principle is that the public key can unlock the file signed by the private key, and the private key can unlock the file encrypted by the public key.
Because asymmetric encryption is more complex, the encryption speed is much slower than symmetric encryption, but it provides higher security for sensitive data protection. Common asymmetric encryption algorithms include RSA, Elliptic Curve Cryptography (ECC), and Diffie-Hellman.
Hashing
Hashing is an algorithm that maps data of any length to a fixed-length digital feature code. Taking md5 as an example, it calculates a length 128-bit hash value based on a certain hash function of the file content. Therefore, if two different files are compared, the hash values will be unequal.
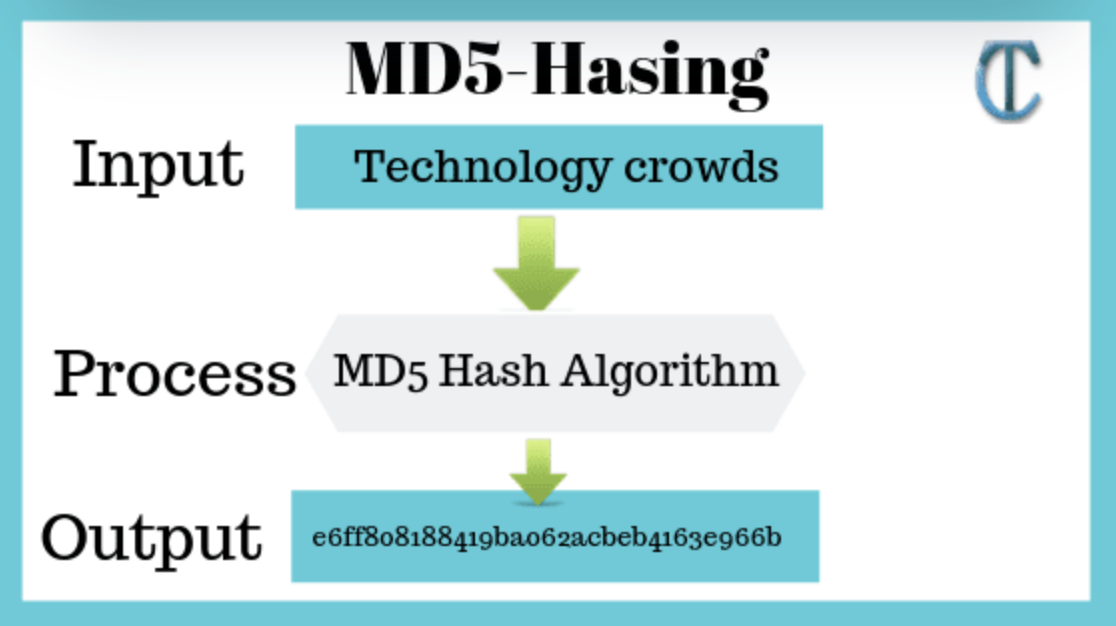
The hash value cannot be restored to the original data, and it is commonly used in data verification, digital signatures, and data storage indexing.
